In the last post we have seen how to implement Site to Site VPN between two Cisco router. Generally these routers are directly connected to the Internet and they also provide internet connectivity to the LAN users.
To illustrate this, I have added a Loopback 0 interface on R4 with the IP address 4.4.4.4/24. Let's assume that it is our destination IP in the Internet.
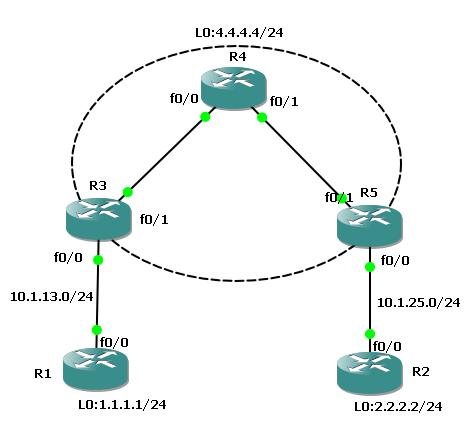
Now for the users at Site A (Loopback 0 of R1) to reach 4.4.4.4, we will have to configure NAT.
Let's configure an ACL which permits all the traffic from 1.1.1.0/24 to any destination along with the other required NAT configuration.
We can test the connectivity by doing telnet from R1 to R4 with source interface as loopback0.

We can now try and ping 2.2.2.2 with the source Loopback0 to establish IPSEC session.

The ping doesn't work. On R2, we can see that the packet are sourced from 10.1.13.1 which is the WAN IP of R1.

The reason being that any traffic with the source as loopback0 is being NATted.

For the VPN to work along with internet access, we have to make sure that the site to site VPN traffic do not get NATted.
To achieve this, we will configure a statement in the ACL which denies the traffic from 1.1.1.0/24 to 2.2.2.0/24.
We have now denied the traffic from Site A to Site B from being NATted. Now let's try to ping 2.2.2.2 from 1.1.1.1

It works now. We can see that the IPSEC tunnel is up.








No comments:
Post a Comment