So far we have seen how to implement site to site VPN
connection with NAT between Cisco routers. The limitation of this setup is that
we cannot run dynamic routing protocol over IPSEC tunnel as IPSEC doesn't support multicast. i.e. if we add more subnets on both the sites
and want them to access via VPN connection, we will have to configure static
routes for each of them.
To overcome this issue, we will configure GRE tunnel between
both the routers. GRE tunnel will allow unicast, multicast and broadcast
traffic between both the routers.
Let’s create tunnel interface on R1 and R2. We will chose
the source as the local WAN interface of the router.
We will now have to permit GRE traffic between both the
routers through IPSEC tunnel. We will modify the ACL 100 and configure an
additional statement on both R1 and R2.
Now Let’s configure EIGRP on both the routers. I have
created a new loopback interface on R1 and R2 which is advertised through the
EIGRP.
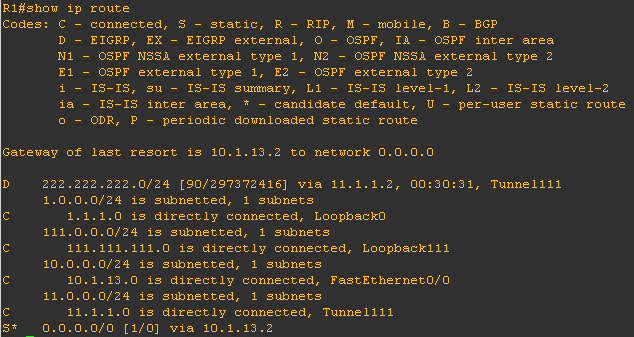
If we check the routing table of R1, we can see
222.222.222.0/24 is received via tunnel interface as an EIGRP route.
Let’s ping 222.222.222.222 from R1.
To confirm that the packets are going over IPSEC tunnel,
we can check the “show crypto IPSEC sa” ouput and see the #pkts encaps/#pkts
decaps counters are increasing.
We don’t need to have the statement to permit 1.1.1.0/24 to
2.2.2.0/24 and vice versa in ACL 100. We can simply just advertise both these
subnets via EIGRP.
Couple of things to consider when you implement this in
production environment
i.
MTU size:
GRE adds an additional 20-byte IP header and a 4-byte GRE header to each packet
in the tunnel. It is quite a common practice to reduce the MTU size to around 1400
bytes to avoid fragmentation issue.
ii.
IOS
version: If you are running a version of IOS Software Release earlier than
12.2.15 then you have to apply the crypto map on the tunnel interface as well
as the physical interface.
Feel free to comment...











No comments:
Post a Comment