Today we will see how we can configure site-to-site VPN
tunnel between two Cisco routers. As shown in the diagram, R1 and R2 represent routers
at Site A and Site B respectively. I have configured Loopback 0 on R1 with IP
address 1.1.1.1/24 and on R2 with IP address 2.2.2.2/24. Both the loopback
represents LAN subnet at each site. The WAN IP of R1 and R2 are 10.1.13.1 and
10.1.25.1 respectively.
The routers R3, R4 and R5 are ISP routers running OSPF
between them. Here is the output from each router showing basic configuration.
Now let’s do traceroute from R1’s loopback0 to R’2
loopback i.e. 1.1.1.1 to 2.2.2.2
Now, let’s configure IPSEC tunnel from R1 to R2.
i.
First we will configure ISAKMP parameters (Phase
1) and the pre-shared key on both the routers
ii.
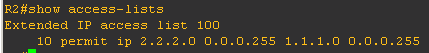
Now we will configure an ACL to define the
interesting traffic
iii.
We can now configure Transform set on both the
routers that will state the encryption and hashing parameters for IPSEC (Phase
2)
iv.
After this, we will have to create “Crypto Map”
to apply Phase 2 parameters on the WAN interface. You can see that we have to
set peer IP address (WAN IP of the opposite router) and use the ACL which
matches the interesting traffic.
v.
The last step is to apply the crypto map on WAN
interface on each router.
Now let’s do ping and traceroute from R1’s loopback to
R2’s loopback (LAN to LAN).
We can see that traffic is now going from R1 to R2
directly through the IPSEC tunnel.
The command “Show crypto ISAKMP SA” can confirm that the
tunnel has been built between the routers and currently in “QM_IDLE” state.
Here is the template which can be used to do generate configs
access-list 100 remark ******Interesting Traffic ******
access-list 100 permit ip <<Source LAN>> <<Destination LAN>>
!
crypto isakmp policy 10
hash sha
authentication pre-share
encryption 3des
group 2
lifetime 86400
!
crypto isakmp key <<Pre-Shared Key>> address <<Remote Peer IP>>
!
crypto ipsec transform-set TRANSFORM_SET esp-3des esp-sha-hmac
mode tunnel
!
crypto map VPN_MAP 1 ipsec-isakmp
set peer <<Remote Peer IP>>
set transform-set TRANSFORM_SET
match address 100
!
interface FastEthernet 0/0
crypto map VPN_MAP

















Thank you for this excellent explanation.
ReplyDeleteCan I kindly request you to answer the below asked questions please?
1) Lifetime set in the above example to create IKE phase is 86400 seconds(24 Hours).
What happens after 24 hours? If R1 sends a packet to R2 after 24 hours, does recreation of IKE phase 1 takes place?
2) When do we use AH instead of ESP for encapsulation?
If I understand correctly, then AH doesn't support encryption. Is AH being used practically?
Regards,
Chirag
1) The peers negotiate a new SA before completing the lifetime of the existing SA to ensure that a new SA is ready when the existing one expires.
Delete2) AH is not widely used in IPSEC VPN implementation because of the reason you stated. However it is still used for some other stuff such as IPv6 OSPF Authentication.