In this post we will see how we can support multiple VRFs in site to site IPSEC VPN implementation.
We will use the below topology. The routers CE1 and CE2 are connected to the Internet. For simplicity, I have used the private IP addressing for the WAN connectivity.

Ok so the first step is to configure required VRFs on both the CPEs.
We are going to configure two VRFs. One called "INTERNET" and the other one called "CUST".
The WAN interfaces (connected to the Internet) will be part of "INTERNET" VRF while the LAN interfaces connecting to the customer network (Loopback 0 interface in our case) and tunnel interfaces will be part of the "CUST" VRF.
There is a terminology to describe these VRFs. The "INTERNET" vrf is referred to as FVRF (Front VRF) and "CUST" vrf is called IVRF (Internal VRF).
Let's start with the configuration. I have only shown the configuration output from the CE1 as the CE2 configuration should be identical.
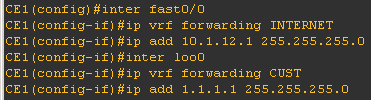
Now we will configure relevant interfaces in each VRF.
The tunnel source and destination are WAN IP addresses of the CEs which are part of the "INTERNET" vrf.
We can now configure the ISAKMP/IPSEC parameters.
For Phase 1 (ISAKMP), we will use AES for encryption, Pre-shared key and DH group 2.
We have also configured keyring named "TEST" for the VRF "INTERNET" with pre-shared key "cisco".
The ISAKMP profile will contain both the FVRF and keyring names.
Now for Phase 2 (IPSEC), we will configure transform-set and IPSEC profile.
This IPSEC profile will not be configured on the tunnel interface.
This completes our GRE/IPSEC configuration however we still need to configure the routing!
The default route is on the internet and points the next hop IP 10.1.12.2
The customer subnets are 1.1.1.0/24 and 4.4.4.0/24 on CE1 and CE2 respectively. They will be reachable through the tunnel next hop IP.
The routing table for both the VRFs look like as below
We will use the below topology. The routers CE1 and CE2 are connected to the Internet. For simplicity, I have used the private IP addressing for the WAN connectivity.

Ok so the first step is to configure required VRFs on both the CPEs.
We are going to configure two VRFs. One called "INTERNET" and the other one called "CUST".
The WAN interfaces (connected to the Internet) will be part of "INTERNET" VRF while the LAN interfaces connecting to the customer network (Loopback 0 interface in our case) and tunnel interfaces will be part of the "CUST" VRF.
There is a terminology to describe these VRFs. The "INTERNET" vrf is referred to as FVRF (Front VRF) and "CUST" vrf is called IVRF (Internal VRF).
Let's start with the configuration. I have only shown the configuration output from the CE1 as the CE2 configuration should be identical.
Now we will configure relevant interfaces in each VRF.
The tunnel source and destination are WAN IP addresses of the CEs which are part of the "INTERNET" vrf.
We can now configure the ISAKMP/IPSEC parameters.
For Phase 1 (ISAKMP), we will use AES for encryption, Pre-shared key and DH group 2.
We have also configured keyring named "TEST" for the VRF "INTERNET" with pre-shared key "cisco".
The ISAKMP profile will contain both the FVRF and keyring names.
Now for Phase 2 (IPSEC), we will configure transform-set and IPSEC profile.
This IPSEC profile will not be configured on the tunnel interface.
The default route is on the internet and points the next hop IP 10.1.12.2
The customer subnets are 1.1.1.0/24 and 4.4.4.0/24 on CE1 and CE2 respectively. They will be reachable through the tunnel next hop IP.
The routing table for both the VRFs look like as below
We can now see that ping from 1.1.1.1 to 4.4.4.4 works successfully.
Whenever IPSEC along with some sort of tunneling mechanism is used, one needs to be careful about the supported MTU size on the link. Due to the various overhead, full 1500 MTU may not be supported.
If you are unsure, please check this link which will help to calculate the overhead you need to take into account while designing the solution.








Thank you very much. Very good post.
ReplyDeleteAmit Makwana
Great and that i have a nifty supply: Can You Hire Someone To Renovate A House average remodel cost
ReplyDelete